![[アップデート] Security Hub に PCI DSS v4.0.1 のセキュリティ基準がサポートされました!](https://images.ctfassets.net/ct0aopd36mqt/wp-thumbnail-e71a738589e583b65670923628e8b6f4/45568b9fd457506bd2f3d6fd304d4b6a/aws-security-hub?w=3840&fm=webp)
[アップデート] Security Hub に PCI DSS v4.0.1 のセキュリティ基準がサポートされました!
この記事は公開されてから1年以上経過しています。情報が古い可能性がありますので、ご注意ください。
こんにちは、AWS 事業本部の平木です。
この度、Security Hub のセキュリティ基準に PCI DSS v4.0.1 が追加されていたためそちらのご紹介です。
v3.2.1 と v4.0.1 の比較
Security Hub において PCI DSS のセキュリティ基準は今まで v3.2.1 がありました。
今回は新しく v4.0.1 がサポートしたので具体的に何が変わったのか見ていきます。
コントロールの比較
下記表は PCI DSS のセキュリティ基準にてサポートしていたコントロール一覧です。
新規追加されたもの、変更なし、削除で見ていきます。
| コントロール ID と名称 | v3.2.1 | v4.0.1 | 変更点 |
|---|---|---|---|
| [ACM.1] Imported and ACM-issued certificates should be renewed after a specified time period | - | ✓ | 新規追加 |
| [ACM.2] RSA certificates managed by ACM should use a key length of at least 2,048 bits | - | ✓ | 新規追加 |
| [APIGateway.9] Access logging should be configured for API Gateway V2 Stages | - | ✓ | 新規追加 |
| [AppSync.2] AWS AppSync should have field-level logging enabled | - | ✓ | 新規追加 |
| [AutoScaling.1] Auto Scaling groups associated with a load balancer should use ELB health checks | ✓ | - | 削除 |
| [AutoScaling.3] Auto Scaling group launch configurations should configure EC2 instances to require Instance Metadata Service Version 2 (IMDSv2) | - | ✓ | 新規追加 |
| [Autoscaling.5] Amazon EC2 instances launched using Auto Scaling group launch configurations should not have Public IP addresses | - | ✓ | 新規追加 |
| [CloudFront.1] CloudFront distributions should have a default root object configured | - | ✓ | 新規追加 |
| [CloudFront.3] CloudFront distributions should require encryption in transit | - | ✓ | 新規追加 |
| [CloudFront.5] CloudFront distributions should have logging enabled | - | ✓ | 新規追加 |
| [CloudFront.6] CloudFront distributions should have WAF enabled | - | ✓ | 新規追加 |
| [CloudFront.9] CloudFront distributions should encrypt traffic to custom origins | - | ✓ | 新規追加 |
| [CloudFront.10] CloudFront distributions should not use deprecated SSL protocols between edge locations and custom origins | - | ✓ | 新規追加 |
| [CloudFront.12] CloudFront distributions should not point to non-existent S3 origins | - | ✓ | 新規追加 |
| [CloudTrail.2] CloudTrail should have encryption at-rest enabled | ✓ | ✓ | 変更なし |
| [CloudTrail.3] At least one CloudTrail trail should be enabled | ✓ | ✓ | 変更なし |
| [CloudTrail.4] CloudTrail log file validation should be enabled | ✓ | ✓ | 変更なし |
| [CloudTrail.5] CloudTrail trails should be integrated with Amazon CloudWatch Logs | ✓ | - | 削除 |
| [CloudTrail.6] Ensure the S3 bucket used to store CloudTrail logs is not publicly accessible | - | ✓ | 新規追加 |
| [CloudTrail.7] Ensure S3 bucket access logging is enabled on the CloudTrail S3 bucket | - | ✓ | 新規追加 |
| [CloudWatch.1] A log metric filter and alarm should exist for usage of the "root" user | ✓ | - | 削除 |
| [CodeBuild.1] CodeBuild Bitbucket source repository URLs should not contain sensitive credentials | ✓ | ✓ | 変更なし |
| [CodeBuild.2] CodeBuild project environment variables should not contain clear text credentials | ✓ | ✓ | 変更なし |
| [CodeBuild.3] CodeBuild S3 logs should be encrypted | - | ✓ | 新規追加 |
| [Config.1] AWS Config should be enabled and use the service-linked role for resource recording | ✓ | - | 削除 |
| [DMS.1] Database Migration Service replication instances should not be public | ✓ | ✓ | 変更なし |
| [DMS.6] DMS replication instances should have automatic minor version upgrade enabled | - | ✓ | 新規追加 |
| [DMS.7] DMS replication tasks for the target database should have logging enabled | - | ✓ | 新規追加 |
| [DMS.8] DMS replication tasks for the source database should have logging enabled | - | ✓ | 新規追加 |
| [DMS.9] DMS endpoints should use SSL | - | ✓ | 新規追加 |
| [DMS.10] DMS endpoints for Neptune databases should have IAM authorization enabled | - | ✓ | 新規追加 |
| [DMS.11] DMS endpoints for MongoDB should have an authentication mechanism enabled | - | ✓ | 新規追加 |
| [DMS.12] DMS endpoints for Redis OSS should have TLS enabled | - | ✓ | 新規追加 |
| [DocumentDB.2] Amazon DocumentDB clusters should have an adequate backup retention period | - | ✓ | 新規追加 |
| [DocumentDB.3] Amazon DocumentDB manual cluster snapshots should not be public | - | ✓ | 新規追加 |
| [DocumentDB.4] Amazon DocumentDB clusters should publish audit logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [DynamoDB.7] DynamoDB Accelerator clusters should be encrypted in transit | - | ✓ | 新規追加 |
| [EC2.1] Amazon EBS snapshots should not be publicly restorable | ✓ | - | 削除 |
| [EC2.2] VPC default security groups should not allow inbound or outbound traffic | ✓ | - | 削除 |
| [EC2.6] VPC flow logging should be enabled in all VPCs | ✓ | - | 削除 |
| [EC2.8] EC2 instances should use Instance Metadata Service Version 2 (IMDSv2) | - | ✓ | 新規追加 |
| [EC2.12] Unused Amazon EC2 EIPs should be removed | ✓ | - | 削除 |
| [EC2.13] Security groups should not allow ingress from 0.0.0.0/0 or ::/0 to port 22 | ✓ | ✓ | 変更なし |
| [EC2.14] Security groups should not allow ingress from 0.0.0.0/0 or ::/0 to port 3389 | - | ✓ | 新規追加 |
| [EC2.15] Amazon EC2 subnets should not automatically assign public IP addresses | - | ✓ | 新規追加 |
| [EC2.16] Unused Network Access Control Lists should be removed | - | ✓ | 新規追加 |
| [EC2.21] Network ACLs should not allow ingress from 0.0.0.0/0 to port 22 or port 3389 | - | ✓ | 新規追加 |
| [EC2.25] Amazon EC2 launch templates should not assign public IPs to network interfaces | - | ✓ | 新規追加 |
| [EC2.51] EC2 Client VPN endpoints should have client connection logging enabled | - | ✓ | 新規追加 |
| [EC2.53] EC2 security groups should not allow ingress from 0.0.0.0/0 to remote server administration ports | - | ✓ | 新規追加 |
| [EC2.54] EC2 security groups should not allow ingress from ::/0 to remote server administration ports | - | ✓ | 新規追加 |
| [EC2.170] EC2 launch templates should use Instance Metadata Service Version 2 (IMDSv2) | - | ✓ | 新規追加 |
| [EC2.171] EC2 VPN connections should have logging enabled | - | ✓ | 新規追加 |
| [ECR.1] ECR private repositories should have image scanning configured | - | ✓ | 新規追加 |
| [ECS.2] ECS services should not have public IP addresses assigned to them automatically | - | ✓ | 新規追加 |
| [ECS.8] Secrets should not be passed as container environment variables | - | ✓ | 新規追加 |
| [ECS.10] ECS Fargate services should run on the latest Fargate platform version | - | ✓ | 新規追加 |
| [ECS.16] ECS task sets should not automatically assign public IP addresses | - | ✓ | 新規追加 |
| [EFS.4] EFS access points should enforce a user identity | - | ✓ | 新規追加 |
| [EKS.1] EKS cluster endpoints should not be publicly accessible | - | ✓ | 新規追加 |
| [EKS.2] EKS clusters should run on a supported Kubernetes version | - | ✓ | 新規追加 |
| [EKS.3] EKS clusters should use encrypted Kubernetes secrets | - | ✓ | 新規追加 |
| [EKS.8] EKS clusters should have audit logging enabled | - | ✓ | 新規追加 |
| [ELB.1] Application Load Balancer should be configured to redirect all HTTP requests to HTTPS | ✓ | - | 削除 |
| [ELB.3] Classic Load Balancer listeners should be configured with HTTPS or TLS termination | - | ✓ | 新規追加 |
| [ELB.4] Application Load Balancer should be configured to drop invalid http headers | - | ✓ | 新規追加 |
| [ELB.8] Classic Load Balancers with SSL listeners should use a predefined security policy that has strong AWS Configuration | - | ✓ | 新規追加 |
| [ELB.12] Application Load Balancer should be configured with defensive or strictest desync mitigation mode | - | ✓ | 新規追加 |
| [ELB.14] Classic Load Balancer should be configured with defensive or strictest desync mitigation mode | - | ✓ | 新規追加 |
| [EMR.1] Amazon EMR cluster primary nodes should not have public IP addresses | - | ✓ | 新規追加 |
| [EMR.2] Amazon EMR block public access setting should be enabled | - | ✓ | 新規追加 |
| [ES.1] Elasticsearch domains should have encryption at-rest enabled | ✓ | - | 削除 |
| [ES.2] Elasticsearch domains should not be publicly accessible | ✓ | ✓ | 変更なし |
| [ES.3] Elasticsearch domains should encrypt data sent between nodes | - | ✓ | 新規追加 |
| [ES.5] Elasticsearch domains should have audit logging enabled | - | ✓ | 新規追加 |
| [ES.8] Connections to Elasticsearch domains should be encrypted using the latest TLS security policy | - | ✓ | 新規追加 |
| [ElastiCache.2] ElastiCache (Redis OSS) clusters should have auto minor version upgrades enabled | - | ✓ | 新規追加 |
| [ElastiCache.5] ElastiCache replication groups should be encrypted in transit | - | ✓ | 新規追加 |
| [ElastiCache.6] ElastiCache (Redis OSS) replication groups of earlier versions should have Redis OSS AUTH enabled | - | ✓ | 新規追加 |
| [ElasticBeanstalk.2] Elastic Beanstalk managed platform updates should be enabled | - | ✓ | 新規追加 |
| [ElasticBeanstalk.3] Elastic Beanstalk should stream logs to CloudWatch | - | ✓ | 新規追加 |
| [EventBridge.3] EventBridge custom event buses should have a resource-based policy attached | - | ✓ | 新規追加 |
| [GuardDuty.1] GuardDuty should be enabled | ✓ | ✓ | 変更なし |
| [GuardDuty.6] GuardDuty Lambda Protection should be enabled | - | ✓ | 新規追加 |
| [GuardDuty.7] GuardDuty EKS Runtime Monitoring should be enabled | - | ✓ | 新規追加 |
| [GuardDuty.9] GuardDuty RDS Protection should be enabled | - | ✓ | 新規追加 |
| [GuardDuty.10] GuardDuty S3 Protection should be enabled | - | ✓ | 新規追加 |
| [IAM.1] IAM policies should not allow full "*" administrative privileges | ✓ | - | 削除 |
| [IAM.2] IAM users should not have IAM policies attached | ✓ | - | 削除 |
| [IAM.3] IAM users' access keys should be rotated every 90 days or less | - | ✓ | 新規追加 |
| [IAM.4] IAM root user access key should not exist | ✓ | - | 削除 |
| [IAM.5] MFA should be enabled for all IAM users that have a console password | - | ✓ | 新規追加 |
| [IAM.6] Hardware MFA should be enabled for the root user | ✓ | ✓ | 変更なし |
| [IAM.7] Password policies for IAM users should have strong configurations | - | ✓ | 新規追加 |
| [IAM.8] Unused IAM user credentials should be removed | ✓ | ✓ | 変更なし |
| [IAM.9] MFA should be enabled for the root user | ✓ | ✓ | 変更なし |
| [IAM.10] Password policies for IAM users should have strong AWS Configurations | ✓ | ✓ | 変更なし |
| [IAM.11] Ensure IAM password policy requires at least one uppercase letter | - | ✓ | 新規追加 |
| [IAM.12] Ensure IAM password policy requires at least one lowercase letter | - | ✓ | 新規追加 |
| [IAM.13] Ensure IAM password policy requires at least one symbol | - | ✓ | 新規追加 |
| [IAM.14] Ensure IAM password policy requires at least one number | - | ✓ | 新規追加 |
| [IAM.16] Ensure IAM password policy prevents password reuse | - | ✓ | 新規追加 |
| [IAM.17] Ensure IAM password policy expires passwords within 90 days or less | - | ✓ | 新規追加 |
| [IAM.18] Ensure a support role has been created to manage incidents with AWS Support | - | ✓ | 新規追加 |
| [IAM.19] MFA should be enabled for all IAM users | ✓ | ✓ | 変更なし |
| [Inspector.1] Amazon Inspector EC2 scanning should be enabled | - | ✓ | 新規追加 |
| [Inspector.2] Amazon Inspector ECR scanning should be enabled | - | ✓ | 新規追加 |
| [Inspector.3] Amazon Inspector Lambda code scanning should be enabled | - | ✓ | 新規追加 |
| [Inspector.4] Amazon Inspector Lambda standard scanning should be enabled | - | ✓ | 新規追加 |
| [KMS.4] AWS KMS key rotation should be enabled | ✓ | ✓ | 変更なし |
| [Lambda.1] Lambda function policies should prohibit public access | ✓ | ✓ | 変更なし |
| [Lambda.2] Lambda functions should use supported runtimes | - | ✓ | 新規追加 |
| [Lambda.3] Lambda functions should be in a VPC | ✓ | - | 削除 |
| [MQ.2] ActiveMQ brokers should stream audit logs to CloudWatch | - | ✓ | 新規追加 |
| [MQ.3] Amazon MQ brokers should have automatic minor version upgrade enabled | - | ✓ | 新規追加 |
| [MSK.1] MSK clusters should be encrypted in transit among broker nodes | - | ✓ | 新規追加 |
| [MSK.3] MSK Connect connectors should be encrypted in transit | - | ✓ | 新規追加 |
| [Neptune.2] Neptune DB clusters should publish audit logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [Neptune.3] Neptune DB cluster snapshots should not be public | - | ✓ | 新規追加 |
| [Opensearch.1] OpenSearch domains should have encryption at rest enabled | ✓ | - | 削除 |
| [Opensearch.2] OpenSearch domains should not be publicly accessible | ✓ | - | 削除 |
| [Opensearch.5] OpenSearch domains should have audit logging enabled | - | ✓ | 新規追加 |
| [Opensearch.10] OpenSearch domains should have the latest software update installed | - | ✓ | 新規追加 |
| [RDS.1] RDS snapshot should be private | ✓ | - | 削除 |
| [RDS.2] RDS DB Instances should prohibit public access | ✓ | ✓ | 変更なし |
| [RDS.9] RDS DB instances should publish logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [RDS.13] RDS automatic minor version upgrades should be enabled | - | ✓ | 新規追加 |
| [RDS.20] Existing RDS event notification subscriptions should be configured for critical database instance events | - | ✓ | 新規追加 |
| [RDS.21] An RDS event notifications subscription should be configured for critical database parameter group events | - | ✓ | 新規追加 |
| [RDS.22] An RDS event notifications subscription should be configured for critical database security group events | - | ✓ | 新規追加 |
| [RDS.24] RDS Database clusters should use a custom administrator username | - | ✓ | 新規追加 |
| [RDS.25] RDS database instances should use a custom administrator username | - | ✓ | 新規追加 |
| [RDS.34] Aurora MySQL DB clusters should publish audit logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [RDS.35] RDS DB clusters should have automatic minor version upgrade enabled | - | ✓ | 新規追加 |
| [RDS.36] RDS for PostgreSQL DB instances should publish logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [RDS.37] Aurora PostgreSQL DB clusters should publish logs to CloudWatch Logs | - | ✓ | 新規追加 |
| [Redshift.1] Amazon Redshift clusters should prohibit public access | ✓ | ✓ | 変更なし |
| [Redshift.2] Connections to Amazon Redshift clusters should be encrypted in transit | - | ✓ | 新規追加 |
| [Redshift.4] Amazon Redshift clusters should have audit logging enabled | - | ✓ | 新規追加 |
| [Redshift.15] Redshift security groups should allow ingress on the cluster port only from restricted origins | - | ✓ | 新規追加 |
| [Route53.2] Route 53 public hosted zones should log DNS queries | - | ✓ | 新規追加 |
| [S3.1] S3 general purpose buckets should have block public access settings enabled | ✓ | ✓ | 変更なし |
| [S3.2] S3 general purpose buckets should block public read access | ✓ | - | 削除 |
| [S3.3] S3 general purpose buckets should block public write access | ✓ | - | 削除 |
| [S3.5] S3 general purpose buckets should require requests to use SSL | ✓ | ✓ | 変更なし |
| [S3.7] S3 general purpose buckets should use cross-Region replication | ✓ | - | 削除 |
| [S3.8] S3 general purpose buckets should block public access | - | ✓ | 新規追加 |
| [S3.9] S3 general purpose buckets should have server access logging enabled | - | ✓ | 新規追加 |
| [S3.15] S3 general purpose buckets should have Object Lock enabled | - | ✓ | 新規追加 |
| [S3.17] S3 general purpose buckets should be encrypted at rest with AWS KMS keys | - | ✓ | 新規追加 |
| [S3.19] S3 access points should have block public access settings enabled | - | ✓ | 新規追加 |
| [S3.22] S3 general purpose buckets should log object-level write events | - | ✓ | 新規追加 |
| [S3.23] S3 general purpose buckets should log object-level read events | - | ✓ | 新規追加 |
| [S3.24] S3 Multi-Region Access Points should have block public access settings enabled | - | ✓ | 新規追加 |
| [SSM.1] Amazon EC2 instances should be managed by AWS Systems Manager | ✓ | - | 削除 |
| [SSM.2] Amazon EC2 instances managed by Systems Manager should have a patch compliance status of COMPLIANT after a patch installation | ✓ | ✓ | 変更なし |
| [SSM.3] Amazon EC2 instances managed by Systems Manager should have an association compliance status of COMPLIANT | ✓ | ✓ | 変更なし |
| [SageMaker AI.1] Amazon SageMaker AI notebook instances should not have direct internet access | ✓ | ✓ | 変更なし |
| [SecretsManager.1] Secrets Manager secrets should have automatic rotation enabled | - | ✓ | 新規追加 |
| [SecretsManager.2] Secrets Manager secrets configured with automatic rotation should rotate successfully | - | ✓ | 新規追加 |
| [SecretsManager.4] Secrets Manager secrets should be rotated within a specified number of days | - | ✓ | 新規追加 |
| [StepFunctions.1] Step Functions state machines should have logging turned on | - | ✓ | 新規追加 |
| [Transfer.2] Transfer Family servers should not use FTP protocol for endpoint connection | - | ✓ | 新規追加 |
| [WAF.1] AWS WAF Classic Global Web ACL logging should be enabled | - | ✓ | 新規追加 |
| [WAF.11] AWS WAF web ACL logging should be enabled | - | ✓ | 新規追加 |
傾向
v4.0.1 になって変わった傾向を見ていきます。
コントロール数
単純にコントロール数が大幅に増えました。
v.3.2.1 が 42 個サポートしていたのに対して、
v4.0.1 では 112 個サポートし、
約 3 倍弱となりました。
ログ監視の強化
v4.0.1 になってからログ取得要件が強化されたように感じました。
RDS,DMS,WAF を初めログの取得を求めるコントロールが多く新規追加されました。
サービスの拡充
v4.0.1 になってから下記カテゴリのサービスが追加されました。
- コンテナ関連(ECS,EKS,ECR)
- データベース関連 (DocumentDB, Neptune)
- セキュリティ関連 (Inspector, WAF)
- アプリケーション配信関連 (CloudFront, APIGateway)
その他にも IAM のパスワードポリシー周りの拡充や暗号化要件が強化されたりなど全体的にセキュリティ面をより一層強化できるものが見られました。
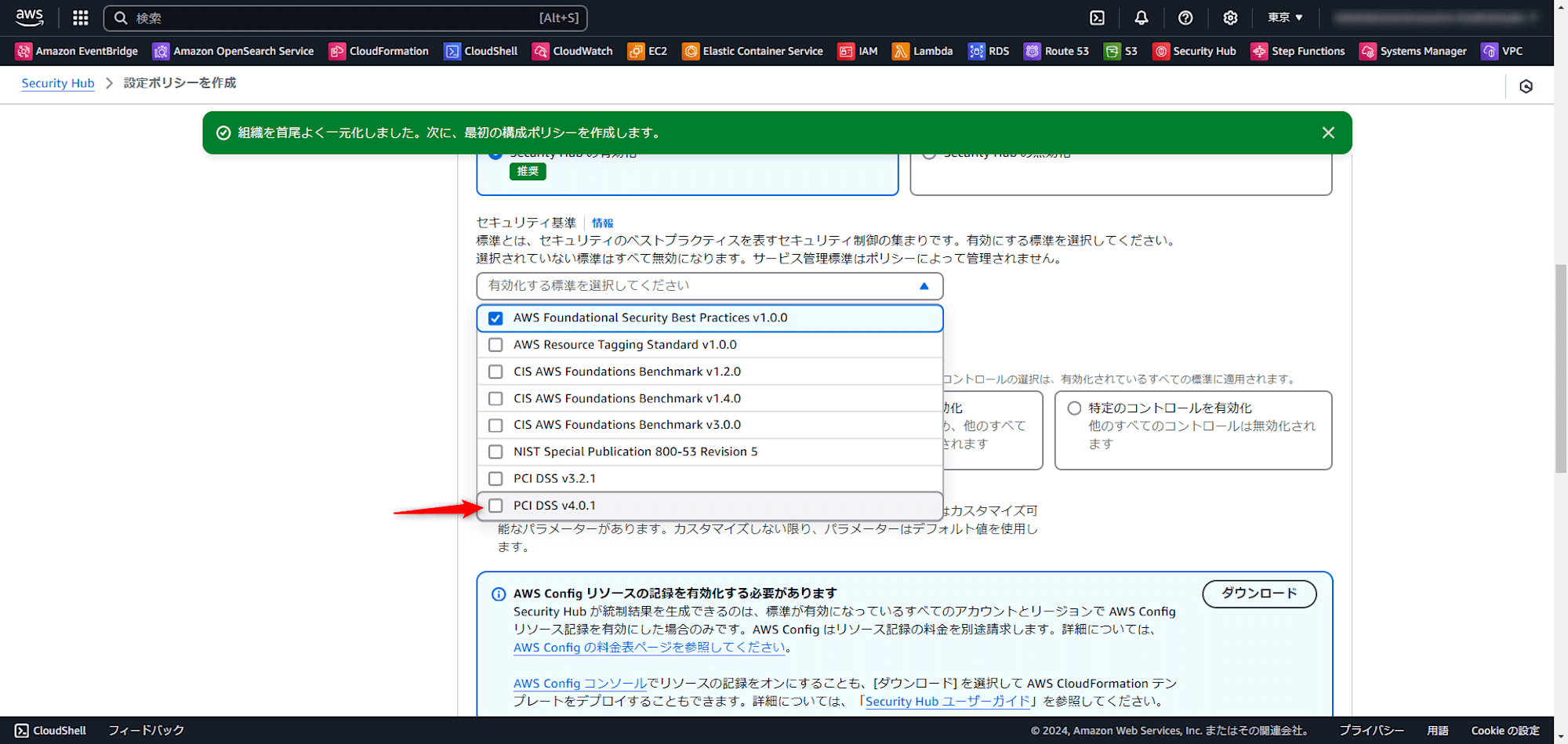
有効化手順
有効化は簡単に実施できます。
Security Hub のセキュリティ基準の画面を確認いただくと PCI DSS v4.0.1 の項目があるため、「標準を有効化」を押します。
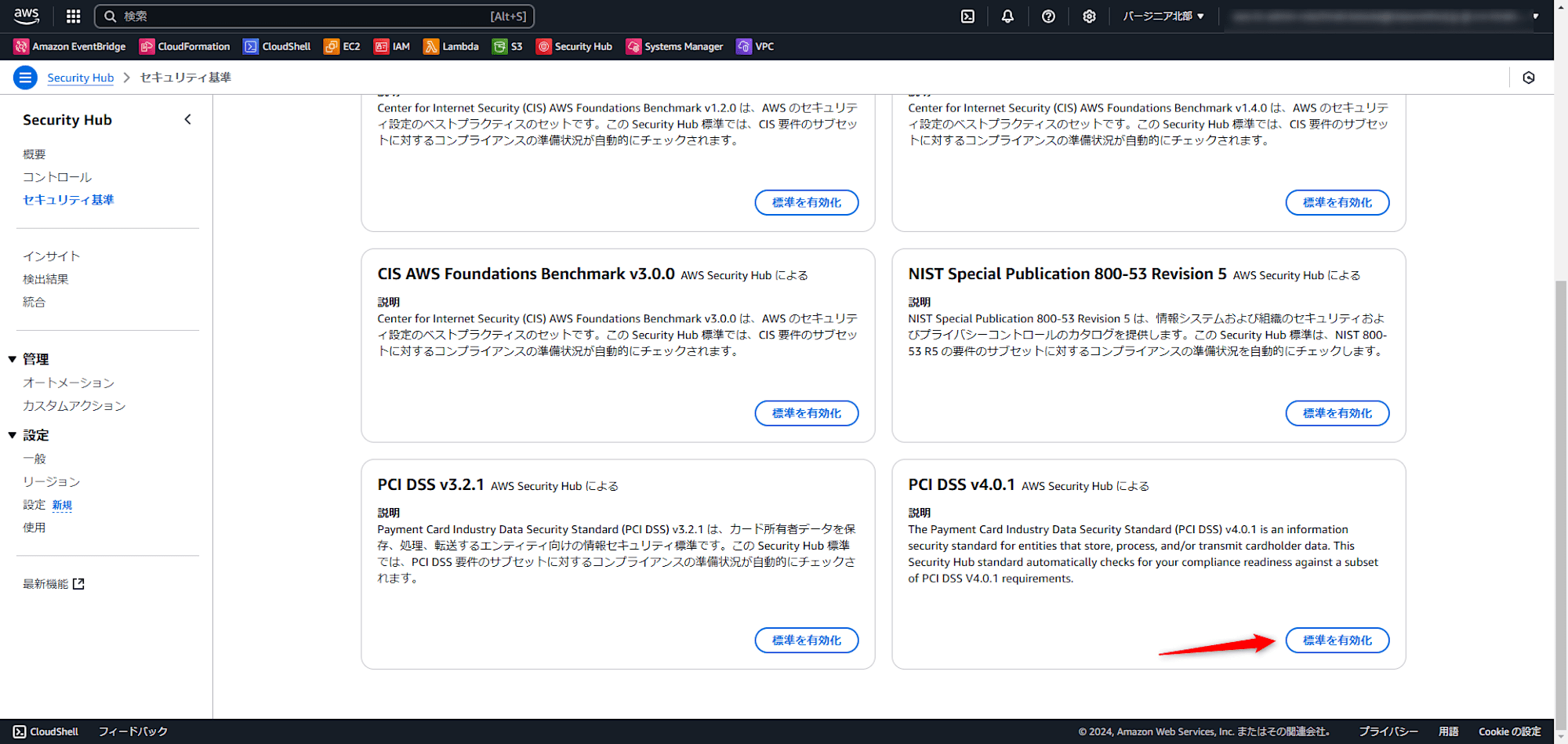
確認画面が出るため、「有効化」を押します。
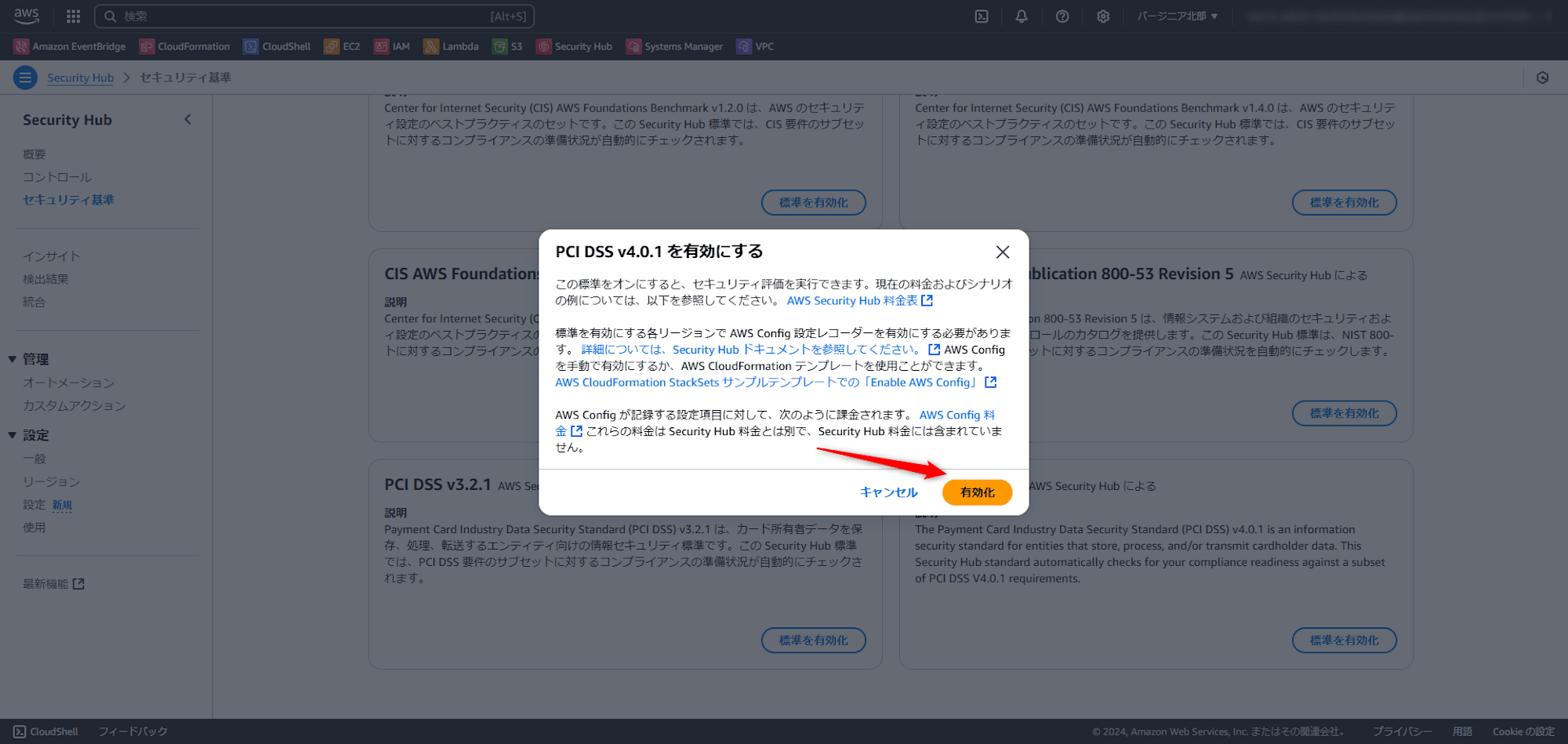
有効化には数分程度かかります。
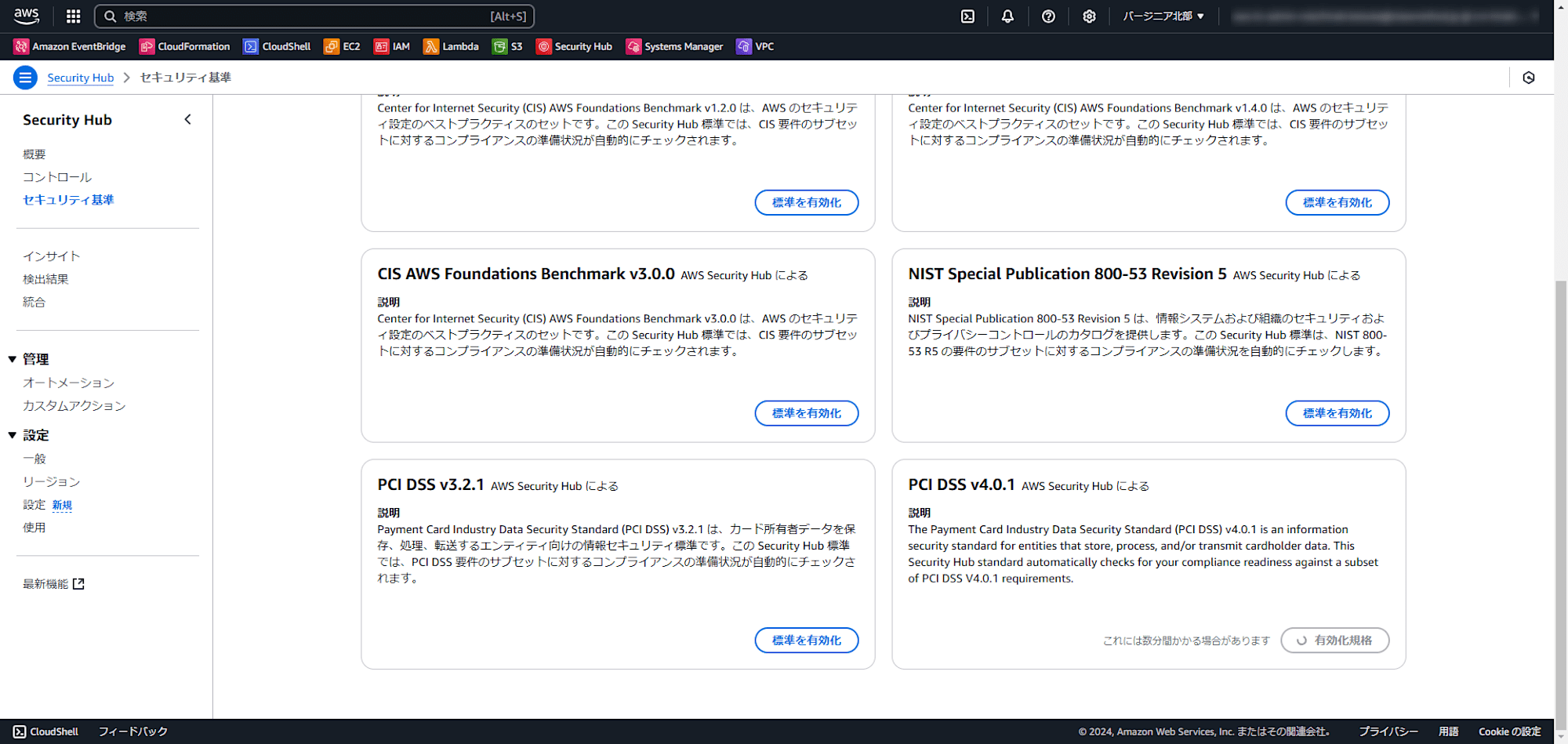
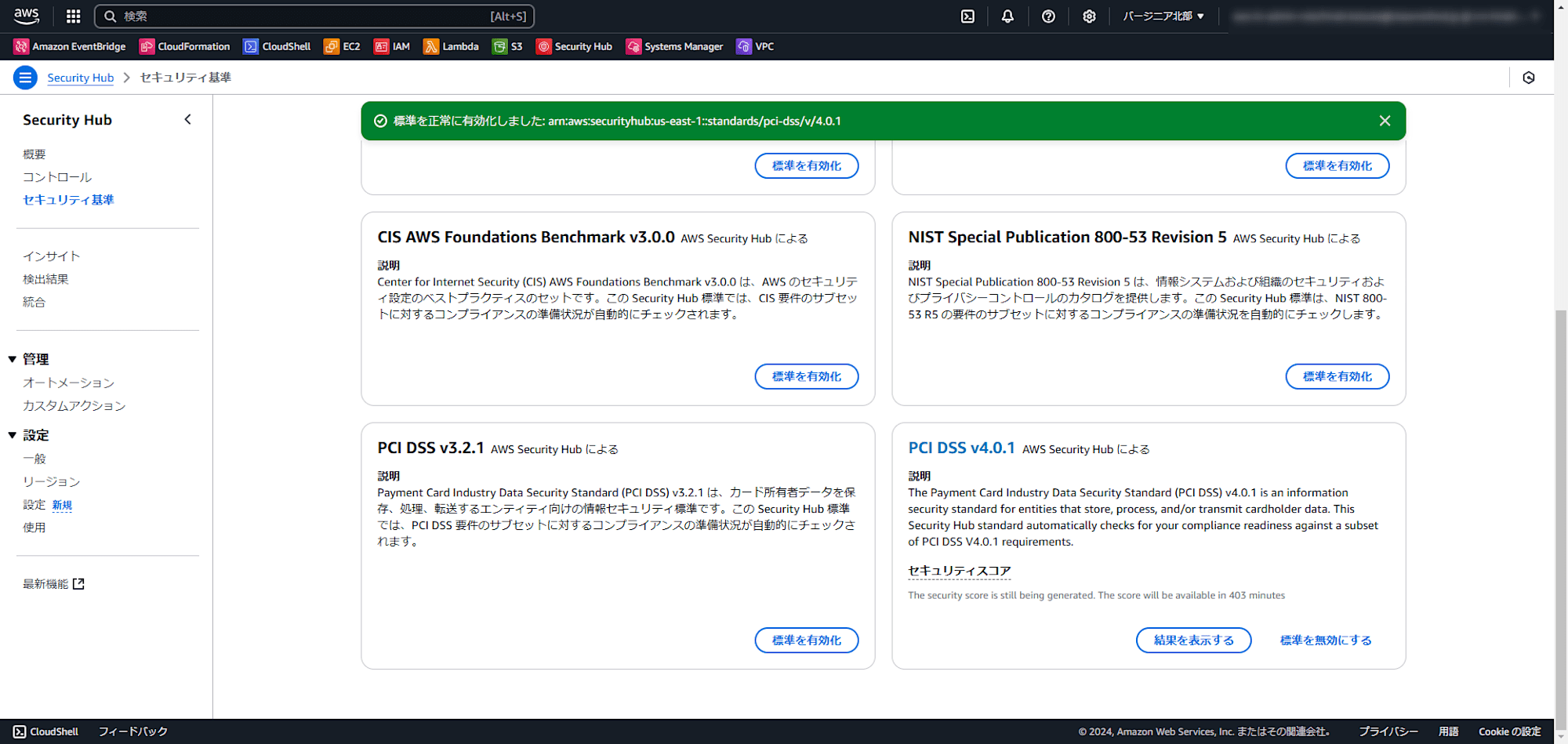
正常に有効化しました、と出れば成功です。
中央設定を活用し Organizations 環境でマルチアカウントに管理している場合は、中央設定上で簡単に有効化できます。
PCI DSS とは
PCI DSS(Payment Card Industry Data Security Standard:ペイメントカード業界データセキュリティ基準)は、VISA や MasterCard などの大手カードブランドが共同で策定した、クレジットカード情報を安全に取り扱うための国際的なセキュリティ基準です。
詳しくはこちらのブログをご参照ください。
おまけ
差分表を作成したためぜひ有効活用してみてください。
Markdown テーブル
| コントロールID | v3.2.1 | v4.0.1 | 変更点 |
|--------------|---------|---------|--------|
| ACM.1 | - | ✓ | 新規追加 |
| ACM.2 | - | ✓ | 新規追加 |
| APIGateway.9 | - | ✓ | 新規追加 |
| AppSync.2 | - | ✓ | 新規追加 |
| AutoScaling.1 | ✓ | - | 削除 |
| AutoScaling.3 | - | ✓ | 新規追加 |
| Autoscaling.5 | - | ✓ | 新規追加 |
| CloudFront.1 | - | ✓ | 新規追加 |
| CloudFront.3 | - | ✓ | 新規追加 |
| CloudFront.5 | - | ✓ | 新規追加 |
| CloudFront.6 | - | ✓ | 新規追加 |
| CloudFront.9 | - | ✓ | 新規追加 |
| CloudFront.10 | - | ✓ | 新規追加 |
| CloudFront.12 | - | ✓ | 新規追加 |
| CloudTrail.2 | ✓ | ✓ | 変更なし |
| CloudTrail.3 | ✓ | ✓ | 変更なし |
| CloudTrail.4 | ✓ | ✓ | 変更なし |
| CloudTrail.5 | ✓ | - | 削除 |
| CloudTrail.6 | - | ✓ | 新規追加 |
| CloudTrail.7 | - | ✓ | 新規追加 |
| CloudWatch.1 | ✓ | - | 削除 |
| CodeBuild.1 | ✓ | ✓ | 変更なし |
| CodeBuild.2 | ✓ | ✓ | 変更なし |
| CodeBuild.3 | - | ✓ | 新規追加 |
| Config.1 | ✓ | - | 削除 |
| DMS.1 | ✓ | ✓ | 変更なし |
| DMS.6 | - | ✓ | 新規追加 |
| DMS.7 | - | ✓ | 新規追加 |
| DMS.8 | - | ✓ | 新規追加 |
| DMS.9 | - | ✓ | 新規追加 |
| DMS.10 | - | ✓ | 新規追加 |
| DMS.11 | - | ✓ | 新規追加 |
| DMS.12 | - | ✓ | 新規追加 |
| DocumentDB.2 | - | ✓ | 新規追加 |
| DocumentDB.3 | - | ✓ | 新規追加 |
| DocumentDB.4 | - | ✓ | 新規追加 |
| DynamoDB.7 | - | ✓ | 新規追加 |
| EC2.1 | ✓ | - | 削除 |
| EC2.2 | ✓ | - | 削除 |
| EC2.6 | ✓ | - | 削除 |
| EC2.8 | - | ✓ | 新規追加 |
| EC2.12 | ✓ | - | 削除 |
| EC2.13 | ✓ | ✓ | 変更なし |
| EC2.14 | - | ✓ | 新規追加 |
| EC2.15 | - | ✓ | 新規追加 |
| EC2.16 | - | ✓ | 新規追加 |
| EC2.21 | - | ✓ | 新規追加 |
| EC2.25 | - | ✓ | 新規追加 |
| EC2.51 | - | ✓ | 新規追加 |
| EC2.53 | - | ✓ | 新規追加 |
| EC2.54 | - | ✓ | 新規追加 |
| EC2.170 | - | ✓ | 新規追加 |
| EC2.171 | - | ✓ | 新規追加 |
| ECR.1 | - | ✓ | 新規追加 |
| ECS.2 | - | ✓ | 新規追加 |
| ECS.8 | - | ✓ | 新規追加 |
| ECS.10 | - | ✓ | 新規追加 |
| ECS.16 | - | ✓ | 新規追加 |
| EFS.4 | - | ✓ | 新規追加 |
| EKS.1 | - | ✓ | 新規追加 |
| EKS.2 | - | ✓ | 新規追加 |
| EKS.3 | - | ✓ | 新規追加 |
| EKS.8 | - | ✓ | 新規追加 |
| ELB.1 | ✓ | - | 削除 |
| ELB.3 | - | ✓ | 新規追加 |
| ELB.4 | - | ✓ | 新規追加 |
| ELB.8 | - | ✓ | 新規追加 |
| ELB.12 | - | ✓ | 新規追加 |
| ELB.14 | - | ✓ | 新規追加 |
| EMR.1 | - | ✓ | 新規追加 |
| EMR.2 | - | ✓ | 新規追加 |
| ES.1 | ✓ | - | 削除 |
| ES.2 | ✓ | ✓ | 変更なし |
| ES.3 | - | ✓ | 新規追加 |
| ES.5 | - | ✓ | 新規追加 |
| ES.8 | - | ✓ | 新規追加 |
| ElastiCache.2 | - | ✓ | 新規追加 |
| ElastiCache.5 | - | ✓ | 新規追加 |
| ElastiCache.6 | - | ✓ | 新規追加 |
| ElasticBeanstalk.2 | - | ✓ | 新規追加 |
| ElasticBeanstalk.3 | - | ✓ | 新規追加 |
| EventBridge.3 | - | ✓ | 新規追加 |
| GuardDuty.1 | ✓ | ✓ | 変更なし |
| GuardDuty.6 | - | ✓ | 新規追加 |
| GuardDuty.7 | - | ✓ | 新規追加 |
| GuardDuty.9 | - | ✓ | 新規追加 |
| GuardDuty.10 | - | ✓ | 新規追加 |
| IAM.1 | ✓ | - | 削除 |
| IAM.2 | ✓ | - | 削除 |
| IAM.3 | - | ✓ | 新規追加 |
| IAM.4 | ✓ | - | 削除 |
| IAM.5 | - | ✓ | 新規追加 |
| IAM.6 | ✓ | ✓ | 変更なし |
| IAM.7 | - | ✓ | 新規追加 |
| IAM.8 | ✓ | ✓ | 変更なし |
| IAM.9 | ✓ | ✓ | 変更なし |
| IAM.10 | ✓ | ✓ | 変更なし |
| IAM.11 | - | ✓ | 新規追加 |
| IAM.12 | - | ✓ | 新規追加 |
| IAM.13 | - | ✓ | 新規追加 |
| IAM.14 | - | ✓ | 新規追加 |
| IAM.16 | - | ✓ | 新規追加 |
| IAM.17 | - | ✓ | 新規追加 |
| IAM.18 | - | ✓ | 新規追加 |
| IAM.19 | ✓ | ✓ | 変更なし |
| Inspector.1 | - | ✓ | 新規追加 |
| Inspector.2 | - | ✓ | 新規追加 |
| Inspector.3 | - | ✓ | 新規追加 |
| Inspector.4 | - | ✓ | 新規追加 |
| KMS.4 | ✓ | ✓ | 変更なし |
| Lambda.1 | ✓ | ✓ | 変更なし |
| Lambda.2 | - | ✓ | 新規追加 |
| Lambda.3 | ✓ | - | 削除 |
| MQ.2 | - | ✓ | 新規追加 |
| MQ.3 | - | ✓ | 新規追加 |
| MSK.1 | - | ✓ | 新規追加 |
| MSK.3 | - | ✓ | 新規追加 |
| Neptune.2 | - | ✓ | 新規追加 |
| Neptune.3 | - | ✓ | 新規追加 |
| Opensearch.1 | ✓ | - | 削除 |
| Opensearch.2 | ✓ | - | 削除 |
| Opensearch.5 | - | ✓ | 新規追加 |
| Opensearch.10 | - | ✓ | 新規追加 |
| RDS.1 | ✓ | - | 削除 |
| RDS.2 | ✓ | ✓ | 変更なし |
| RDS.9 | - | ✓ | 新規追加 |
| RDS.13 | - | ✓ | 新規追加 |
| RDS.20 | - | ✓ | 新規追加 |
| RDS.21 | - | ✓ | 新規追加 |
| RDS.22 | - | ✓ | 新規追加 |
| RDS.24 | - | ✓ | 新規追加 |
| RDS.25 | - | ✓ | 新規追加 |
| RDS.34 | - | ✓ | 新規追加 |
| RDS.35 | - | ✓ | 新規追加 |
| RDS.36 | - | ✓ | 新規追加 |
| RDS.37 | - | ✓ | 新規追加 |
| Redshift.1 | ✓ | ✓ | 変更なし |
| Redshift.2 | - | ✓ | 新規追加 |
| Redshift.4 | - | ✓ | 新規追加 |
| Redshift.15 | - | ✓ | 新規追加 |
| Route53.2 | - | ✓ | 新規追加 |
| S3.1 | ✓ | ✓ | 変更なし |
| S3.2 | ✓ | - | 削除 |
| S3.3 | ✓ | - | 削除 |
| S3.5 | ✓ | ✓ | 変更なし |
| S3.7 | ✓ | - | 削除 |
| S3.8 | - | ✓ | 新規追加 |
| S3.9 | - | ✓ | 新規追加 |
| S3.15 | - | ✓ | 新規追加 |
| S3.17 | - | ✓ | 新規追加 |
| S3.19 | - | ✓ | 新規追加 |
| S3.22 | - | ✓ | 新規追加 |
| S3.23 | - | ✓ | 新規追加 |
| S3.24 | - | ✓ | 新規追加 |
| SSM.1 | ✓ | - | 削除 |
| SSM.2 | ✓ | ✓ | 変更なし |
| SSM.3 | ✓ | ✓ | 変更なし |
| SageMaker AI.1 | ✓ | ✓ | 変更なし |
| SecretsManager.1 | - | ✓ | 新規追加 |
| SecretsManager.2 | - | ✓ | 新規追加 |
| SecretsManager.4 | - | ✓ | 新規追加 |
| StepFunctions.1 | - | ✓ | 新規追加 |
| Transfer.2 | - | ✓ | 新規追加 |
| WAF.1 | - | ✓ | 新規追加 |
| WAF.11 | - | ✓ | 新規追加 |
CSV
コントロール ID,v3.2.1,v4.0.1,変更点
ACM.1,-,✓,新規追加
ACM.2,-,✓,新規追加
APIGateway.9,-,✓,新規追加
AppSync.2,-,✓,新規追加
AutoScaling.1,✓,-,削除
AutoScaling.3,-,✓,新規追加
Autoscaling.5,-,✓,新規追加
CloudFront.1,-,✓,新規追加
CloudFront.3,-,✓,新規追加
CloudFront.5,-,✓,新規追加
CloudFront.6,-,✓,新規追加
CloudFront.9,-,✓,新規追加
CloudFront.10,-,✓,新規追加
CloudFront.12,-,✓,新規追加
CloudTrail.2,✓,✓,変更なし
CloudTrail.3,✓,✓,変更なし
CloudTrail.4,✓,✓,変更なし
CloudTrail.5,✓,-,削除
CloudTrail.6,-,✓,新規追加
CloudTrail.7,-,✓,新規追加
CloudWatch.1,✓,-,削除
CodeBuild.1,✓,✓,変更なし
CodeBuild.2,✓,✓,変更なし
CodeBuild.3,-,✓,新規追加
Config.1,✓,-,削除
DMS.1,✓,✓,変更なし
DMS.6,-,✓,新規追加
DMS.7,-,✓,新規追加
DMS.8,-,✓,新規追加
DMS.9,-,✓,新規追加
DMS.10,-,✓,新規追加
DMS.11,-,✓,新規追加
DMS.12,-,✓,新規追加
DocumentDB.2,-,✓,新規追加
DocumentDB.3,-,✓,新規追加
DocumentDB.4,-,✓,新規追加
DynamoDB.7,-,✓,新規追加
EC2.1,✓,-,削除
EC2.2,✓,-,削除
EC2.6,✓,-,削除
EC2.8,-,✓,新規追加
EC2.12,✓,-,削除
EC2.13,✓,✓,変更なし
EC2.14,-,✓,新規追加
EC2.15,-,✓,新規追加
EC2.16,-,✓,新規追加
EC2.21,-,✓,新規追加
EC2.25,-,✓,新規追加
EC2.51,-,✓,新規追加
EC2.53,-,✓,新規追加
EC2.54,-,✓,新規追加
EC2.170,-,✓,新規追加
EC2.171,-,✓,新規追加
ECR.1,-,✓,新規追加
ECS.2,-,✓,新規追加
ECS.8,-,✓,新規追加
ECS.10,-,✓,新規追加
ECS.16,-,✓,新規追加
EFS.4,-,✓,新規追加
EKS.1,-,✓,新規追加
EKS.2,-,✓,新規追加
EKS.3,-,✓,新規追加
EKS.8,-,✓,新規追加
ELB.1,✓,-,削除
ELB.3,-,✓,新規追加
ELB.4,-,✓,新規追加
ELB.8,-,✓,新規追加
ELB.12,-,✓,新規追加
ELB.14,-,✓,新規追加
EMR.1,-,✓,新規追加
EMR.2,-,✓,新規追加
ES.1,✓,-,削除
ES.2,✓,✓,変更なし
ES.3,-,✓,新規追加
ES.5,-,✓,新規追加
ES.8,-,✓,新規追加
ElastiCache.2,-,✓,新規追加
ElastiCache.5,-,✓,新規追加
ElastiCache.6,-,✓,新規追加
ElasticBeanstalk.2,-,✓,新規追加
ElasticBeanstalk.3,-,✓,新規追加
EventBridge.3,-,✓,新規追加
GuardDuty.1,✓,✓,変更なし
GuardDuty.6,-,✓,新規追加
GuardDuty.7,-,✓,新規追加
GuardDuty.9,-,✓,新規追加
GuardDuty.10,-,✓,新規追加
IAM.1,✓,-,削除
IAM.2,✓,-,削除
IAM.3,-,✓,新規追加
IAM.4,✓,-,削除
IAM.5,-,✓,新規追加
IAM.6,✓,✓,変更なし
IAM.7,-,✓,新規追加
IAM.8,✓,✓,変更なし
IAM.9,✓,✓,変更なし
IAM.10,✓,✓,変更なし
IAM.11,-,✓,新規追加
IAM.12,-,✓,新規追加
IAM.13,-,✓,新規追加
IAM.14,-,✓,新規追加
IAM.16,-,✓,新規追加
IAM.17,-,✓,新規追加
IAM.18,-,✓,新規追加
IAM.19,✓,✓,変更なし
Inspector.1,-,✓,新規追加
Inspector.2,-,✓,新規追加
Inspector.3,-,✓,新規追加
Inspector.4,-,✓,新規追加
KMS.4,✓,✓,変更なし
Lambda.1,✓,✓,変更なし
Lambda.2,-,✓,新規追加
Lambda.3,✓,-,削除
MQ.2,-,✓,新規追加
MQ.3,-,✓,新規追加
MSK.1,-,✓,新規追加
MSK.3,-,✓,新規追加
Neptune.2,-,✓,新規追加
Neptune.3,-,✓,新規追加
Opensearch.1,✓,-,削除
Opensearch.2,✓,-,削除
Opensearch.5,-,✓,新規追加
Opensearch.10,-,✓,新規追加
RDS.1,✓,-,削除
RDS.2,✓,✓,変更なし
RDS.9,-,✓,新規追加
RDS.13,-,✓,新規追加
RDS.20,-,✓,新規追加
RDS.21,-,✓,新規追加
RDS.22,-,✓,新規追加
RDS.24,-,✓,新規追加
RDS.25,-,✓,新規追加
RDS.34,-,✓,新規追加
RDS.35,-,✓,新規追加
RDS.36,-,✓,新規追加
RDS.37,-,✓,新規追加
Redshift.1,✓,✓,変更なし
Redshift.2,-,✓,新規追加
Redshift.4,-,✓,新規追加
Redshift.15,-,✓,新規追加
Route53.2,-,✓,新規追加
S3.1,✓,✓,変更なし
S3.2,✓,-,削除
S3.3,✓,-,削除
S3.5,✓,✓,変更なし
S3.7,✓,-,削除
S3.8,-,✓,新規追加
S3.9,-,✓,新規追加
S3.15,-,✓,新規追加
S3.17,-,✓,新規追加
S3.19,-,✓,新規追加
S3.22,-,✓,新規追加
S3.23,-,✓,新規追加
S3.24,-,✓,新規追加
SSM.1,✓,-,削除
SSM.2,✓,✓,変更なし
SSM.3,✓,✓,変更なし
SageMaker AI.1,✓,✓,変更なし
SecretsManager.1,-,✓,新規追加
SecretsManager.2,-,✓,新規追加
SecretsManager.4,-,✓,新規追加
StepFunctions.1,-,✓,新規追加
Transfer.2,-,✓,新規追加
WAF.1,-,✓,新規追加
WAF.11,-,✓,新規追加
参考
おわりに
今回は、Security Hub にセキュリティ基準で追加された PCI DSS v4.0.1 についてご紹介しました。
こちらの記事も合わせてご覧ください!
この記事がどなたかの役に立つと嬉しいです。







